By acquiring Level 3, CenturyLink immediately enhanced the visibility it has into traffic flows across its large network.
But the company said that with this new set of capabilities, it now has a responsibility to ensure it can shield and thwart attacks coming from the public internet to its customer base.
Chris Richter, VP of global security services for CenturyLink, told FierceTelecom that since the service provider is one of the largest internet transit providers, it takes this role even more seriously.
“We do a lot of work to keep the internet running and protect the internet not as a service, but we have to act as good stewards of the internet because we control and see so much of it,” Richter said.
Richter said that the responsibility to ensure that the internet can run isn’t just the job of CenturyLink, but of the service provider community overall.
“We believe that all network service providers should do what they can within the realms of economic feasibility to protect the internet,” Richter said. “For that reason, when we know there’s bad actors on our backbone using our infrastructure, we want to keep it as clean as we possibly can, which is what compels us to take down the 35 bot net organizations every month we do.”
RELATED: CenturyLink expands threat management tools to monitor 114B sessions per day
Completing the Level 3 acquisition enhanced CenturyLink's cybersecurity capabilities by offering business customers expanded visibility into global threats.
These capabilities have enabled CenturyLink to gain visibility into over 114 billion NetFlow sessions and 1.3 billion security events per day, responding to and mitigating roughly 120 DDoS attacks per day and removing approximately 35 command and control networks per month.
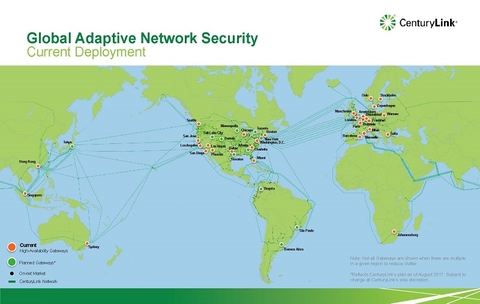
The service provider built up an additional collection of NetFlow infrastructure to accommodate and pull in all of the CenturyLink network NetFlow data into the threat analysis engines. Previously, Level 3 had done this on its own network before it was acquired by CenturyLink.
Richter said that the process to enhance the NetFlow infrastructure was a smooth one.
“It was fairly straightforward to do,” Richter said. “All we had to do was make the additional investment in the new collectors and direct that NetFlow information to our Threat Intelligence Labs where the collectors are and adjust for a lot more information.”
But this was not just about fulfilling an internal need. Richter noted that CenturyLink business customers asked for this new capability.
“This was something that the legacy CenturyLink customer base had been asking for,” Richter said. “When they heard about what the legacy Level 3 portfolio offered, they wanted that level of visibility and granularity on the CenturyLink side.”